Legacy TLS cipher support in Firefox
By stretch | Wednesday, October 12, 2016 at 5:45 p.m. UTC
After upgrading Firefox recently, I noticed that I could no longer access certain embedded devices via HTTPS. It seems that recent versions of Firefox and Chrome no longer support certain TLS ciphers due to recently discovered vulnerabilities. That's all well and good, except the error returned offers no recourse if you need to connect anyway.
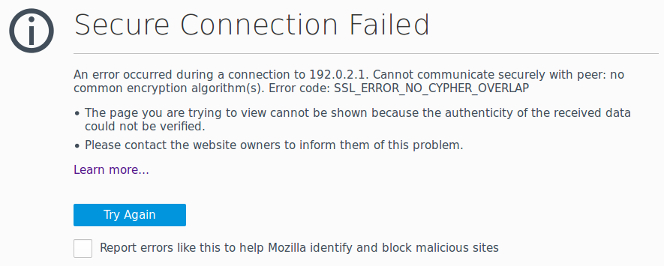
Firefox returns the error SSL_ERROR_NO_CYPHER_OVERLAP with no option to temporarily allow connectivity. (Chrome reports a similar error named ERR_SSL_VERSION_OR_CIPHER_MISMATCH.) Presumably, this choice was made by the developers with the intention of forcing people to upgrade outdated devices. Unfortunately, in order to upgrade an out-of-date device, we typically must first be able to connect to it. I wasted a fair bit of time digging up a solution, so I figured I'd document the workaround here for when I inevitably run into this problem again a year from now and have forgotten what I did.
If you're not able to work around this restriction by using plain HTTP or by connecting via an alternate interface (e.g. SSH), Firefox does allow you to manually enter an exception to cipher validation. Open a new tab and navigate to about:config. (Acknowledge the warning if one is presented.) Search for "security.tls" and double-click the setting named security.tls.insecure_fallback_hosts.
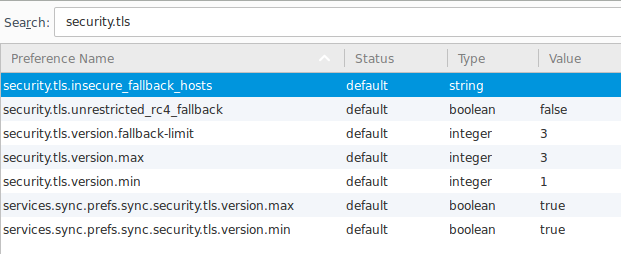
Add the hostnames and/or IP addresses to which you need to connect. Separate multiple entries using commas (no spaces). Click OK when finished and you should see your entered hosts listed in the about:config list. Now, try to connect to one of the desired hosts again via HTTPS. The warning should no longer appear.
Note: You might still encounter other warnings relevant to HTTPS, such as one indicating an unsigned certificate (SEC_ERROR_UNKNOWN_ISSUER). You should be able to dismiss these warnings separately.
Finally, I've noticed that once I've upgraded a device's firmware to support modern ciphers and reconnected to it successfully, it disappears from the security.tls.insecure_fallback_hosts list.
Posted in Tips and Tricks
Comments
October 12, 2016 at 6:22 p.m. UTC
Hi Jeremy, thanks for sharing your findings on this. I ran into the same problem a couple of times and have used older, portable versions of Firefox as my workaround.
Kind regards, Jaap de Vos
October 12, 2016 at 7:45 p.m. UTC
Good to see this. Just today I came across this and resorted to using IE (for those devices affected of course).
November 2, 2016 at 8:24 p.m. UTC
Well done Kiddo...I so wish we could afford hiring you. Pure gold.
November 7, 2016 at 12:32 p.m. UTC
Good info. I understand why they do this but quite frankly for managing legacy equipment I can't just update because it's EOL or in production, and he'll, it's internal only anyway, I hate that they keep taking the override settings away. I am stuck on FF ESR 38 because of this problem, but if this works, I may finally be able to upgrade.
November 30, 2016 at 5:35 p.m. UTC
Has anyone encountered the problem when you still see:
Cannot communicate securely with peer: no common encryption algorithm(s). Error code: SSL_ERROR_NO_CYPHER_OVERLAP
Even after adding it to the fallback hosts?
AS
December 2, 2016 at 4:37 p.m. UTC
Ugh, yes, thank you! We have a similar problem with the Java on a poorly maintained Avocent unit. Frustrating enough that I'm soon approaching the fire axe patching methodology...
December 29, 2016 at 10:30 a.m. UTC
@Amrinder: yes, it seems that it does not work in Firefox 50.
February 23, 2017 at 6:29 p.m. UTC
Yes, it seems Firefox has patched this workaround, but luckily they allow you to download old versions! I just downloaded Firefox 49, made sure auto-updates was disabled, and then I was finally able to manage some Juniper firewalls that use older ciphers and need to get replaced.
Not sure how long this link will be good for, but this is the page to get older versions - https://support.mozilla.org/t5/Install-and-Update/Install-an-older-version-of-Firefox/ta-p/1564. If it goes bad, just search for "old version of firefox", that is how I found it.
Good stuff Stretch!
February 24, 2017 at 8:24 p.m. UTC
Ha. I have an ancient Firefox portable copy (I think it's 3.6) Keep it around for all sorts of stupid things. RC4 protocol and TLS are the latest two, but I've seen Mikrotik devices and random embedded appliances that don't seem to want to play nice with anything else. Portable app, only opened when needed.
FYI; IE doesn't bypass some of these issues on newer versions of Windows. For example, 8.1 and 10 have both been patched to kill RC4 and older TLS: you have to turn them on at the OS level for IE to function. I prefer to containerize these sorts of vulnerabilities.
April 27, 2017 at 6:57 a.m. UTC
Good to see this. Just today I came across this and resorted to using chrome. unfortunately
April 29, 2017 at 4:06 a.m. UTC
Thanks Jeremy. I encounter the same thing last few days too.
October 10, 2017 at 6:56 a.m. UTC
Excellent Tips. I think it will be very helpful for me. 400-101 dumps
