Capturing serial traffic on Ethernet with RITE
By stretch | Monday, October 26, 2009 at 7:19 a.m. UTC
When it comes to capturing packets traversing an Ethernet switch, Cisco's Switched Port Analyzer (SPAN) feature is an invaluable tool. However, replicating traffic across router interfaces poses a problem: SPAN can't be used on routers, as the underlying hardware doesn't support it. Additionally, the variety of interface types can complicate packet capturing on routers; how do we sniff a serial interface with Wireshark running on a laptop, for example?
Cisco's solution is Router IP Traffic Export (RITE). Introduced in IOS 12.3(4)T, RITE allows for the replication of packets from one interface to another on software-switched platforms in the same manner SPAN operates on hardware-based switches. RITE allows us to "SPAN" across routed interfaces, even across disparate medium types.
Consider a scenario in which we need a sniffer or IDS to capture IP traffic traversing a PPP serial link between two routers.
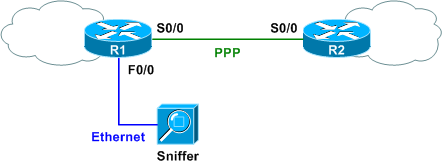
We can enable RITE on R1 to replicate WAN traffic to the Ethernet sniffer. Only two items are needed to configure a minimal RITE profile:
- Physical output interface (the interface connected to our sniffer)
- Destination MAC address for the replicated packets (the MAC address of our sniffer)
We can see from the diagram that our sniffer is attached to FastEthernet0/0, and we'll assume the MAC address of our sniffer is 00-01-02-03-04-05. (Note that as sniffers are generally run in promiscuous mode, any MAC should work in this case. However, RITE won't accept a broadcast MAC address.)
Configuring our RITE profile on R1 is straightforward:
R1(config)# ip traffic-export profile MyProfile R1(conf-rite)# interface f0/0 R1(conf-rite)# mac-address 0001.0203.0405
The above configuration is all that's required for a minimal profile. Additionally, we'll include the bidirectional parameter here to ensure that traffic from both directions is replicated (versus only inbound traffic).
R1(conf-rite)# bidirectional
We can also optionally specify an access list and/or sampling rate to limit the type and amount of traffic we capture, respectively, with the incoming and outgoing parameters.
R1(conf-rite)# incoming ? access-list Apply standard or extended access lists to exported traffic sample Enable sampling of exported traffic R1(conf-rite)# incoming access-list ? <1-199> IP access list (standard or extended) <1300-2699> IP expanded access list (standard or extended) WORD Access-list name R1(conf-rite)# incoming sample ? one-in-every Export one packet in every
Forgoing these options for this scenario, we are ready to apply our RITE policy to R1's serial interface. Make sure that you exit RITE configuration before entering interface configuration to avoid modifying the interface parameter of the RITE profile.
R1(conf-rite)# exit R1(config)# interface s0/0 R1(config-if)# ip traffic-export apply MyProfile R1(config-if)# %RITE-5-ACTIVATE: Activated IP traffic export on interface Serial0/0
The command show ip traffic-export verifies our configuration:
R1# show ip traffic-export
Router IP Traffic Export Parameters
Monitored Interface Serial0/0
Export Interface FastEthernet0/0
Destination MAC address 0001.0203.0405
bi-directional traffic export is on
Output IP Traffic Export Information Packets/Bytes Exported 0/0
Packets Dropped 0
Sampling Rate one-in-every 1 packets
No Access List configured
Input IP Traffic Export Information Packets/Bytes Exported 15/1500
Packets Dropped 0
Sampling Rate one-in-every 1 packets
No Access List configured
Profile MyProfile is Active
All IP traffic traversing R1's Serial0/0 interface is now being replicated out R1's FastEthernet0/0 interface toward our sniffer, with one observed exception. Only transit traffic is replicated; inbound traffic destined for R1 itself is also replicated, however outbound traffic generated locally by R1 is not. Also note that only IP traffic is being replicated, and we lose any lower-layer headers (like PPP) due to the change in medium.
Posted in Random, Tips and Tricks
Comments
October 26, 2009 at 1:51 p.m. UTC
Nice feature, thanks Stretch.
By the way, looks like there's a typo, 'Traffice'.
October 26, 2009 at 1:56 p.m. UTC
Good one, Jeremy. I didn't even know this feature existed. For God's sake, do NOT tell my security guys; they'll want to implement this all over the company.
October 26, 2009 at 4:33 p.m. UTC
sounds interesting.
a feature, i personally recommend, is Embedded Packet Capture introduced in 12.4(20)T
October 26, 2009 at 4:43 p.m. UTC
The acronym is awfully close to RITA (RFC 2321) :)
October 29, 2009 at 9:53 a.m. UTC
vey nice feature, does it use cpu resources or are the packets cef switched?
November 12, 2009 at 3:32 a.m. UTC
Cool feature, what we used to do in the old days is take an old router and use it as a debug router. Now for serial ports you can do the same. Cool.
November 13, 2009 at 9:21 p.m. UTC
Oh Man....learn something new every day. I'm going to re-tool my lab and see what I can see right away. Good stuff.....thanks Stretch.....
December 1, 2009 at 6:03 p.m. UTC
This is good stuff! I've done a lot of spans for packet capture, but never knew this was an option for a router. Thanks!
April 27, 2010 at 11:48 a.m. UTC
Hi stretch, thanks for this stuff. I have a question, when you do something like this:
R1(conf-rite)# interface f0/0
R1(conf-rite)# mac-address 0001.0203.0405
Doesn't it actually change the mac address of interface f0/0 ??
May 8, 2010 at 11:07 a.m. UTC
@rinoel
Notice that "mac-address" command is entered in (conf-rite)# mode not in (config-if)# so it doesn't affect f0/0 mac address.
HTH
Roland
January 26, 2011 at 7:11 p.m. UTC
Could you tell me what IOS image are you using to do this and what hardware? thanks.
