802.1X guest VLANs
By stretch | Tuesday, August 12, 2008 at 8:02 a.m. UTC
Reader Marcus suggested an extension of last week's post on configuring wired 802.1X discussing the use of a guest VLAN. 802.1X includes the capability of defining a guest VLAN in which unauthenticated clients are placed. This can be handy to provide a sort of user-facing demilitarized zone, where guests can connect to the network but only to receive limited services, or to provide temporary restricted access to download software updates.
Configuring a guest VLAN is simple, so long as you understand the concept. We'll continue from the previous example, adding a guest VLAN with access only to the Internet, as depicted here:
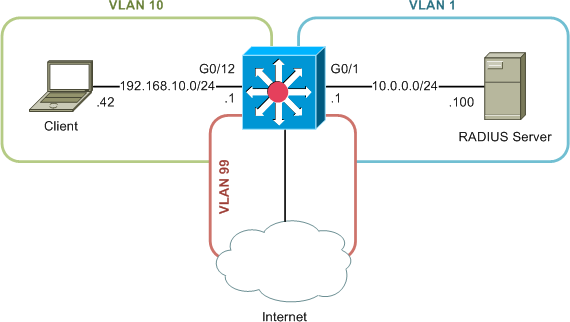
This time, however, we'll assume our client is not 802.1X-capable (if continuing from the previous lab, be sure to disable 802.1X authentication under the network connection properties dialog). Configuring a guest VLAN is as simple as defining the VLAN number appropriately under the desired 802.1X interfaces:
Switch(config)# interface g0/12 Switch(config-if)# dot1x guest-vlan 99 Switch(config-if)# do show run int g0/12 Building configuration... Current configuration : 159 bytes ! interface GigabitEthernet0/12 switchport access vlan 10 switchport mode access dot1x port-control auto dot1x guest-vlan 99
We can see VLAN 99 specified as the guest VLAN under the interface's 802.1X properties.
Switch# show dot1x int g0/12 Supplicant MAC AuthSM State = CONNECTING BendSM State = IDLE PortStatus = UNAUTHORIZED MaxReq = 2 MaxAuthReq = 2 HostMode = Single PortControl = Auto QuietPeriod = 60 Seconds Re-authentication = Disabled ReAuthPeriod = 3600 Seconds ServerTimeout = 30 Seconds SuppTimeout = 30 Seconds TxPeriod = 30 Seconds Guest-Vlan = 99
Now we can connect our client. The switch will prompt for authentication but, receiving no response, will eventually (after roughly 90 seconds) give up and place the client in the guest VLAN.
Switch# show dot1x int g0/12 Supplicant MAC AuthSM State = AUTHENTICATED(GUEST_VLAN) BendSM State = IDLE PortStatus = AUTHORIZED(GUEST-VLAN) MaxReq = 2 MaxAuthReq = 2 HostMode = Multi(GUEST VLAN) PortControl = Auto QuietPeriod = 60 Seconds Re-authentication = Disabled ReAuthPeriod = 3600 Seconds ServerTimeout = 30 Seconds SuppTimeout = 30 Seconds TxPeriod = 30 Seconds Guest-Vlan = 99 Switch# show int g0/12 switchport | i Access Access Mode VLAN: 99 (VLAN0099)
The unauthenticated client can now only send traffic to VLAN 99; it will have to authenticate successfully before it can be placed in its permanent VLAN, VLAN 10.
Note that the guest VLAN is intended to be used for clients which have no ability to authenticate; those clients which fail authentication deserve additional consideration. Prior to IOS 12.2(25)SE, clients which fail authentication are simply placed in the guest VLAN. With the introduction of 12.2(25)SE, clients which fail authentication remain in their assigned VLAN, unable to communicate. This behavior can be reverted to the older style with the command dot1x guest-vlan supplicant under global configuration.
IOS 12.2(25)SED introduced another option: restricted VLANs. A restricted VLAN can be defined in addition to a guest VLAN, to handle clients which attempt and fail authentication. Defining a restricted (or "authentication failure") VLAN is similar to defining a guest VLAN:
Switch(config-if)# dot1x auth-fail vlan
Posted in Security
Comments
August 12, 2008 at 1:12 p.m. UTC
Great write up! Thanks
August 12, 2008 at 3:17 p.m. UTC
I've found you've got to tweak the authentication timers and retries for Guest VLAN access. Many times the client will assign itself a 169.254.x.x address before the switch decides put the PC in the guest VLAN. I've found the following works well:
dot1x timeout quiet-period 10 ! wait 10 seconds between auth requests dot1x timeout tx-period 5 ! wait 5 seconds to hear EAP from the client dot1x max-req 1 ! quit trying to re-authenticate after 1 try
August 12, 2008 at 3:39 p.m. UTC
Thanks...i was just trying to explain this to a colleague
August 13, 2008 at 10:12 p.m. UTC
I am interested in knowing how do you draw those beautiful topology diagrams :-)
July 7, 2009 at 1:11 p.m. UTC
only this web site clear my doubt about dot1x auth-fail vlan .
Big Thanks from my Heart
September 29, 2009 at 12:43 a.m. UTC
Hello! Base klooper appropriate for my english jer, buti very nice re say gJ$)Kd!!!.
