Configuring OSPFv2 Between Cisco and Force10
By stretch | Monday, November 8, 2010 at 2:22 a.m. UTC
Fellow blogger Stuart Howlette recently shared his thoughts on multi-vendor networking and the need to learn technologies themselves rather than the manner in which they are implemented on a given platform. I couldn't agree more; but how much overlap is there in practice? Perhaps an experiment is in order...
Last week, I announced that Force10 Networks had generously sponsored one of their S25 switches for the community lab. Having no prior experience with Force10's OS, FTOS, I was intrigued by how similar it was to the very familiar territory of Cisco IOS. I devised a simple three-router OSPF lab with the FTOS box in the middle to see how someone with only IOS experience might fare.
OSPFv2 Configuration on FTOS
Our example topology is below. R1 and R3 are Cisco IOS routers which have already been configured. (For an IOS OSPF refresher, check out the wiki article.
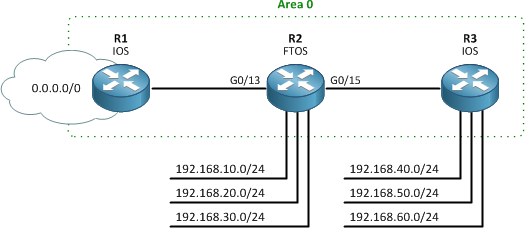
So, let's begin. First, we'll need to create the OSPFv2 process. This happens to be accomplished exactly as on IOS.
Force10(conf)# router ? bgp Border Gateway Protocol (BGP) ospf Open Shortest Path First (OSPF) rip Routing Information Protocol (RIP) Force10(conf)# router ospf 1 Force10(conf-router_ospf-1)# router-id 2.2.2.2 Changing router-id will bring down existing OSPF adjacency [y/n]: y Force10(conf-router_ospf-1)#
Note that unlike IOS, FTOS prompts you to reset the OSPF process immediately after modifying the router ID.
Next we'll assign areas to the routed interfaces. This is done with the network command; we don't have the option on FTOS to assign OSPF areas under interface configuration. Happily though, we're able to use CIDR notation for the specification of network masks.
Force10(conf-router_ospf-1)# network 10.0.12.0/24 area 0 Force10(conf-router_ospf-1)# network 10.0.23.0/24 area 10 Force10(conf-router_ospf-1)# network 192.168.0.0/16 area 10
We'll complete our configuration by enabling OSPF MD5 authentication under interface configuration. Since this only a lab, we'll use the same key for both links.
Force10(conf-router_ospf-1)# interface g0/13 Force10(conf-if-gi-0/13)# ip ospf message-digest-key 1 md5 Cisco2Force10 Force10(conf-if-gi-0/13)# interface g0/15 Force10(conf-if-gi-0/15)# ip ospf message-digest-key 1 md5 Cisco2Force10
Note that we need only one line to enable MD5 configuration under FTOS, versus an additional line to explicitly state the authentication mode on IOS. Attempting to configure plaintext authentication as well results in an error:
Force10(conf-if-gi-0/15)# ip ospf authentication-key foo % Error: Authentication scheme conflict, Unconfigure current scheme.
At this point, we should form adjacencies with the two neighboring IOS routers.
Force10# show ip ospf neighbor Neighbor ID Pri State Dead Time Address Interface Area 1.1.1.1 1 FULL/DR 00:00:31 10.0.12.1 Gi 0/13 0 3.3.3.3 1 FULL/DR 00:00:34 10.0.23.3 Gi 0/15 10
Note that R2 is not elected as the DR on either link, as the other two routers were both already functioning and had each elected itself as the DR.
We can use some familiar show commands to glean more information about the OSPF process and routes:
Force10# show ip protocols
Routing Protocol is "ospf 1"
Router ID is 2.2.2.2
It is an Area Border Router
Area Routing for Networks
0 10.0.12.0/24
10 10.0.23.0/24
10 192.168.30.0/24
10 192.168.20.0/24
10 192.168.10.0/24
Force10# show ip ospf interface
GigabitEthernet 0/13 is up, line protocol is up
Internet Address 10.0.12.2/24, Area 0
Process ID 1, Router ID 2.2.2.2, Network Type BROADCAST, Cost: 1
Transmit Delay is 1 sec, State BDR, Priority 1
Designated Router (ID) 1.1.1.1, Interface address 10.0.12.1
Backup Designated Router (ID) 2.2.2.2, Interface address 10.0.12.2
Timer intervals configured, Hello 10, Dead 40, Wait 40, Retransmit 5
Hello due in 00:00:07
Message digest authentication enabled
Youngest key id is 1
Neighbor Count is 1, Adjacent neighbor count is 1
Adjacent with neighbor 1.1.1.1 (Designated Router)
GigabitEthernet 0/15 is up, line protocol is up
Internet Address 10.0.23.2/24, Area 10
Process ID 1, Router ID 2.2.2.2, Network Type BROADCAST, Cost: 1
Transmit Delay is 1 sec, State BDR, Priority 1
Designated Router (ID) 3.3.3.3, Interface address 10.0.23.3
Backup Designated Router (ID) 2.2.2.2, Interface address 10.0.23.2
Timer intervals configured, Hello 10, Dead 40, Wait 40, Retransmit 5
Hello due in 00:00:05
Message digest authentication enabled
Youngest key id is 1
Neighbor Count is 1, Adjacent neighbor count is 1
Adjacent with neighbor 3.3.3.3 (Designated Router)
...
Force10# show ip route
Codes: C - connected, S - static, R - RIP,
B - BGP, IN - internal BGP, EX - external BGP,LO - Locally Originated,
O - OSPF, IA - OSPF inter area, N1 - OSPF NSSA external type 1,
N2 - OSPF NSSA external type 2, E1 - OSPF external type 1,
E2 - OSPF external type 2, i - IS-IS, L1 - IS-IS level-1,
L2 - IS-IS level-2, IA - IS-IS inter area, * - candidate default,
> - non-active route, + - summary route
Gateway of last resort is 10.0.12.1 to network 0.0.0.0
Destination Gateway Dist/Metric Last Change
----------- ------- ----------- -----------
*O E2 0.0.0.0/0 via 10.0.12.1, Gi 0/13 110/1 00:01:13
C 10.0.12.0/24 Direct, Gi 0/13 0/0 00:02:06
C 10.0.23.0/24 Direct, Gi 0/15 0/0 00:02:07
C 192.168.10.0/24 Direct, Lo 10 0/0 00:24:54
C 192.168.20.0/24 Direct, Lo 20 0/0 00:24:48
C 192.168.30.0/24 Direct, Lo 30 0/0 00:24:43
O 192.168.40.1/32 via 10.0.23.3, Gi 0/15 110/2 00:01:13
O 192.168.50.1/32 via 10.0.23.3, Gi 0/15 110/2 00:01:13
O 192.168.60.1/32 via 10.0.23.3, Gi 0/15 110/2 00:01:13
A brief word of caution with regard to OSPF timers: Our routers formed adjacencies without issue because both IOS and FTOS use hello and dead timers of 10 and 40 seconds, respectively, on Ethernet interfaces. The FTOS configuration guide notes a subtle difference between IOS and FTOS timer calculation, though:
In FTOS the OSPF dead interval value is, by default, set to 40 seconds, and is independent of the OSPF hello interval. Configuring a hello interval does not change the dead interval in FTOS. In contrast, the OSPF dead interval on a Cisco router is, by default, four times as long as the hello interval. Changing the hello interval on the Cisco router automatically changes the dead interval as well.
In short, if you adjust the default hello timer on FTOS, don't neglect to modify the dead timer manually as well; it won't be automatically updated like on IOS.
Conclusion
Anyone with moderate Cisco IOS experience should be able to implement basic configurations like these on Force10 FTOS without even consulting the documentation (of course this isn't to say that you shouldn't). Granted, adopting a new vendor's interface won't always be this trivial, but I hope this helps highlight the necessity of learning how protocols work, not just memorizing commands.
The entire relevant portion of the finished FTOS configuration is included below.
interface GigabitEthernet 0/13 ip address 10.0.12.2/24 ip ospf message-digest-key 1 md5 7 7ca1a8757de1e45573cfd9a267c04957 no shutdown ! interface GigabitEthernet 0/15 ip address 10.0.23.2/24 ip ospf message-digest-key 1 md5 7 7ca1a8757de1e45573cfd9a267c04957 no shutdown ! router ospf 1 router-id 2.2.2.2 network 10.0.12.0/24 area 0 network 10.0.23.0/24 area 10 network 192.168.0.0/16 area 10
Comments
November 8, 2010 at 2:31 a.m. UTC
Heh, could have been summed up as "they're pretty much the same".
If anyone has any F10 questions, feel free to ask. I just finished a large rollout of S series stacks and C series chassis. As far as 10GigE goes, F10 is hard to beat at the access/distribution layers.
November 8, 2010 at 8:36 a.m. UTC
Thanks for the mention :)
I quite like the look of the configuration on the Force10, it does look like it wouldn't take too long to pick up.
One thing though
"This is done with the network command; we don't have the option on FTOS to assign OSPF areas under interface configuration. Happily though, we're able to use CIDR notation for the specification of network masks."
This displeases me, it further helps the notion that in OSPF that you are advertising networks, and not enabling OSPF on interfaces with the network command. The amount of times I've had to explain this to people, I need to get it tattoo'd on me somewhere for easy reference...
November 8, 2010 at 11:28 a.m. UTC
Hey Stretch,
great article, I like it when CLIs are similar, makes us think more about the underlying technology and protocols then.
Stuh84,
you're right about the "network" command, the amount of confusion around this command is immense and the amount of different explanations I've gotten which contradict eachother is staggering.
Would make a good subject for an article, along with the passive interface command...hint hint.
Thanks again ya'll,
Paul
November 8, 2010 at 3:12 p.m. UTC
@stuh84: True; I prefer the per-interface approach myself. However I dislike the labor of calculating and and typing out wildcard masks. Theoretically you should be able to use a /32 mask to specify individual interface addresses, similar to IOS' 0.0.0.0. Haven't tried it though.
@Paulkil: Not a bad idea.
November 8, 2010 at 3:48 p.m. UTC
@IPv6Freely: I'd encourage folks to take a look at Brocade's NetIron series of gear as well. The MLXe has capacity today for: 4 to 32 slots 2x100Gbps, 8x10Gbps, 48x1000Base-T, 20x1Gbps SFP all at full line rate with all services enabled. Pricing is very attractive. They're frugal on power consumption. LAGs with 2-32 ports (odd numbers not a problem). And the CLI is very comparable with IOS.
November 8, 2010 at 8:48 p.m. UTC
Heh, wow! If it didn't say FTOS as the hostname, I would probably think it's Cisco. I really like the way FTOS outputs the "show ip route". It has the next hop, as well as the exit interface. With IOS, you always have to take an extra step to figure out that interface.
November 9, 2010 at 12:45 a.m. UTC
Hi Stretch,
nice post (as always ;-)
But i think there's a little mistake:
Note that unlike IOS, FTOS prompts you to reset the IOS process immediately after modifying the router ID.
I think it should be called "the OSPF process".
Keep it up !
Regards from Germany,
Alex
