Creating ACL entries in Wireshark
By stretch | Thursday, October 29, 2009 at 7:36 a.m. UTC
Wireshark is an awesome tool, and it seems like every time I use it I discover another little nugget of awesomeness. In this case, it was Wireshark's ability to generate ACL and firewall entries on the fly from a captured packet.
Let's assume we've captured some unauthorized traffic traversing the firewall: an IRC sesion. We can examine the capture with Wireshark to confirm that the traffic should be denied by the security policy, and automatically generate an ACL entry (ACE) to match the appropriate packets. First, select one of the packets from the suspect session:
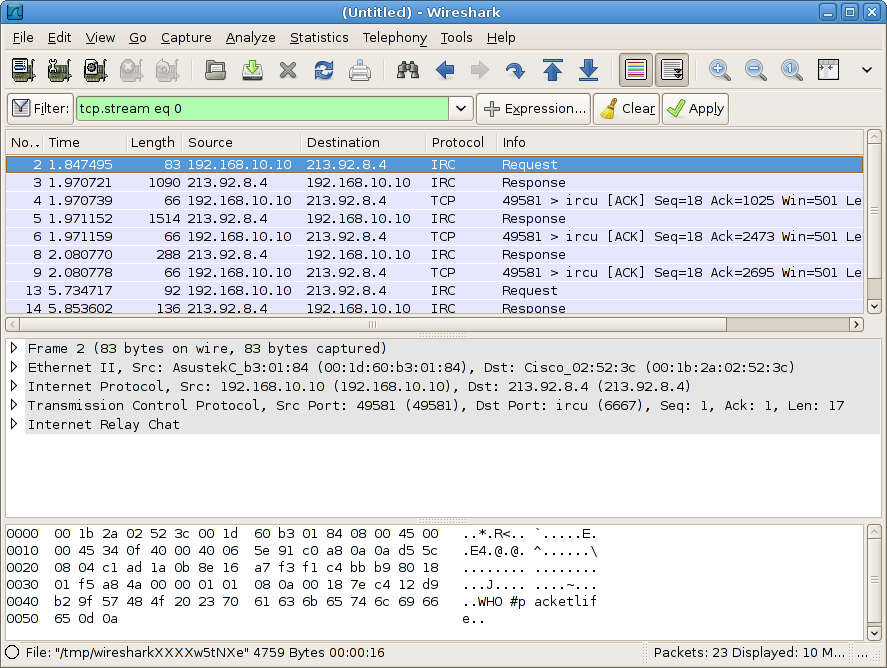
Then, navigate to Tools > Firewall ACL Rules.
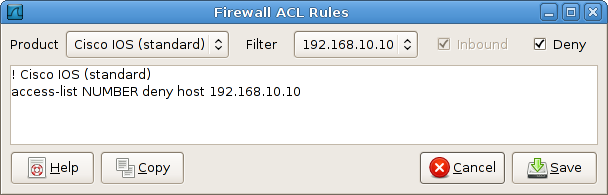
Wireshark supports several types of syntax, including Cisco IOS standard and extended ACLs, IP Filter, IPFirewall, Net Filter, Packet Filter, and Windows Firewall. Selecting Cisco IOS (extended) offers several levels of granularity: we can filter the source or destination host, TCP port, or both. Additionally, we can toggle the Inbound switch to swap source and destination addresses, and the Deny switch to toggle between permit and deny actions.
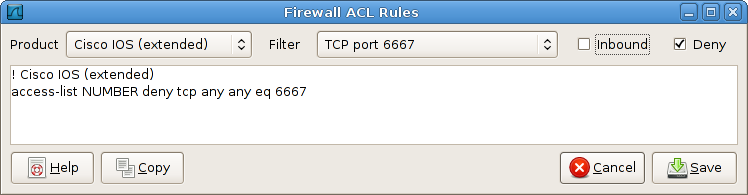
The generated syntax can then be copied and pasted directly into an ACL.
While veteran engineers may find this little more than a convenience feature, it can be an excellent learning tool for students to experiment with creating ACEs to match real-world traffic.
Posted in Tips and Tricks
Comments
October 29, 2009 at 9:05 a.m. UTC
Nice article... i never looked into this feature but the IPtables options is pretty cool...
October 29, 2009 at 9:23 a.m. UTC
Very cool!
October 29, 2009 at 12:58 p.m. UTC
Cool. Always look forward to reading your articles.
October 29, 2009 at 1:02 p.m. UTC
That is pretty cool.
October 29, 2009 at 1:43 p.m. UTC
While my old-school manner dictates that I do it by hand, I have used this feature to show non-network people some of the innards of ACLEs; it helps them understand why I tell them to provide IP addresses, protocols, and ports when requesting access through a firewall or router.
Great article!
October 31, 2009 at 1:20 a.m. UTC
really a nice article.
regards shivlu jain
November 2, 2009 at 2:47 a.m. UTC
Great article! This is a very cool feature...
November 5, 2009 at 4:41 p.m. UTC
Using Wireshark 1.0.7 on Ubuntu 9.04, this feature can be found in the Analyize>Firewall ACL Rules. Nice feature especially when writing IPtables rules or pf rules since I don't write these rules as often as router ACLs or firewall ACLs.
