Quick and dirty packet capture data extraction
By stretch | Monday, July 13, 2009 at 12:58 a.m. UTC
If you ever find yourself needing to reconstruct binary data contained within a packet capture, there is a simple way to do so on the fly using only Wireshark and a utility called foremost. Reference the attached packet capture containing a JPEG image downloaded via HTTP to play along.
Step 1: Isolate the desired data stream
This is most easily done by selecting a packet within the stream containing the data you want to extract and selecting "Follow TCP (or UDP) Stream" from the right-click context menu.
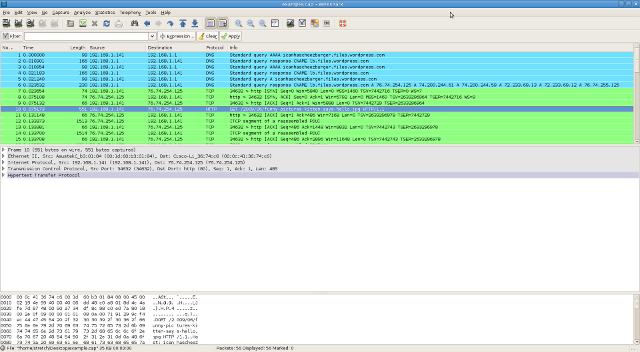
Wireshark applies a display filter to the packet list so that only packets from the selected stream are shown, and it invokes the stream content window shown below.
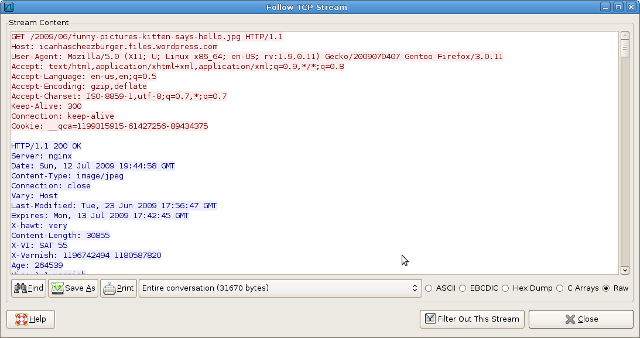
Step 2: Extract raw unidirectional data
Wireshark marks transmitted and received data in red and blue, respectively. For the purpose of this example, we're only interested in the received data, so we restrict the stream parser to show only inbound (blue) packets by selecting that direction from the option at bottom.
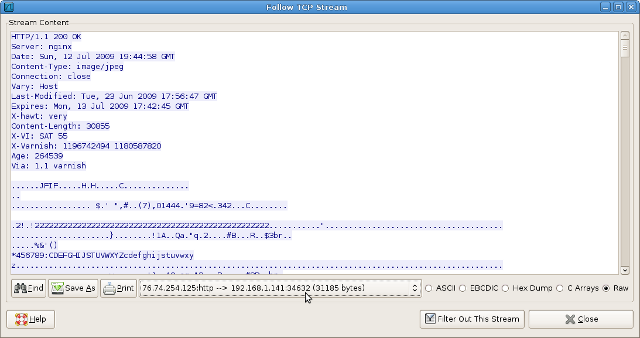
Now to extract this data. Ensure that the Raw option is selected and click Save As to export the binary data. For our example, I've saved the dump to disk as "example.raw".
Step 3: Data carving with foremost
What we have now is an HTTP response and a JPEG image smooshed together in a single binary blob; this isn't of much use.
$ file example.raw example.raw: data
We can use the foremost forensics utility to sift through this blob and extract any recognizable binary data structures (e.g. a JPEG image).
$ foremost -v -i example.raw Foremost version 1.5.5 by Jesse Kornblum, Kris Kendall, and Nick Mikus Audit File Foremost started at Sun Jul 12 15:59:27 2009 Invocation: foremost -v -i example.raw Output directory: /home/stretch/test/output Configuration file: /etc/foremost.conf Processing: example.raw |------------------------------------------------------------------ File: example.raw Start: Sun Jul 12 15:59:27 2009 Length: 30 KB (31185 bytes) Num Name (bs=512) Size File Offset Comment 0: 00000000.jpg 30 KB 330 *| Finish: Sun Jul 12 15:59:27 2009 1 FILES EXTRACTED jpg:= 1 ------------------------------------------------------------------ Foremost finished at Sun Jul 12 15:59:27 2009
foremost dumps its findings to a directory named output:
$ ls output/ audit.txt jpg $ ls output/jpg/ 00000000.jpg $ file output/jpg/00000000.jpg output/jpg/00000000.jpg: JPEG image data, JFIF standard 1.01
Filenames are assigned as serial identifiers because foremost has no knowledge of their original names, but the data is intact.
There are, of course, more elegant ways to do this, but this simple method is handy when on-the-run or manual one-off analysis is necessary. Some other (open source) tools to check out are:
- NetworkMiner (Windows)
- tcpxtract
- tcpflow
(Thanks to Dave Hull, from whom I shamelessly stole this idea.)
Update
Jeremy L Gaddis pointed out that Wireshark has the (limited) ability to extract data on its own, demonstrated nicely in these two videos: JPEG from the example and a PDF. (Note that foremost may still be necessary for extracting data from protocols other than HTTP.)
Also, Sebastien Raveau suggested tcpflow, which I've added to the list of suggested tools above.
Thanks guys!
Posted in Tips and Tricks
Comments
July 13, 2009 at 1:59 a.m. UTC
You're doing the hard way. Since you're already running wireshark, why not let it do the extraction for you?
July 13, 2009 at 6:22 a.m. UTC
Hey :)
In case you don't know it already, check out tcpflow
It is perfect for doing bulk "follow TCP stream" stuff...
July 13, 2009 at 11:32 a.m. UTC
You should also check out Dave Hull's follow-up post on this matter.
In this post Dave mentions my suggestion for an even simpler method for extracting files using Wirehsark's "Export Selected Packet Bytes…". In the comments Jonathan Ham also mentions an even quicker method that unfortunately only works for HTTP.
My weapon-of-choice for these tasks is of course NetworkMiner, which you also nicely mentioned in your post (thanks!).
July 14, 2009 at 7:12 p.m. UTC
Just for images but still fun when using (an open) WLAN:
http://www.ex-parrot.com/~chris/driftnet/
And there is also dsniff which includes filesnarf to extract files from nfs traffic.
July 22, 2009 at 4:03 a.m. UTC
Another tool which does the same thing is Chaosreader (http://chaosreader.sourceforge.net/), it can also create some pretty funky reports.
August 9, 2010 at 10:18 a.m. UTC
This is the best process i have read for packet capturing.. hope this would help me to capture data from particular location.
September 19, 2010 at 2:40 p.m. UTC
hey fellows,
Im new to all these but i wanna achieve sumthing that is along this line too
Ive got 2 computers connected with ad hoc (WEP) PC1 (windows) and PC2 (windows) However i connected a 3rd computer to the network (ubuntu) I shared a folder on pc2 then transferred series of odinary jpeg files from pc1 to pc 2 using regular copy and paste.
my main goal is to be able to sniff those jpeg files using tools like driftnet that displays the images in real time or to store the wireshark dump and try and convert the raw data back to an image
when i did a search from wireshark, i could see traces of the names of the jpeg i sent...
Would appreciate it if u cld be of assitance
