January contest answer
By stretch | Friday, January 9, 2009 at 10:50 a.m. UTC
The contest is over! The IOS version running on the router at 172.16.232.10: 12.4(9)T1. A bit of crypto savvy was necessary to arrive at the answer...
Probably the first data everyone looked at are the painfully obvious Telnet packets, which carry cleartext console traffic to the router's virtual console (or VTY). Using a packet analyzer, a display filter can be applied to the capture to reconstruct the original data stream. In Wireshark, this is accomplished by right-clicking one of the Telnet packets and selecting Follow TCP Stream from the context menu.
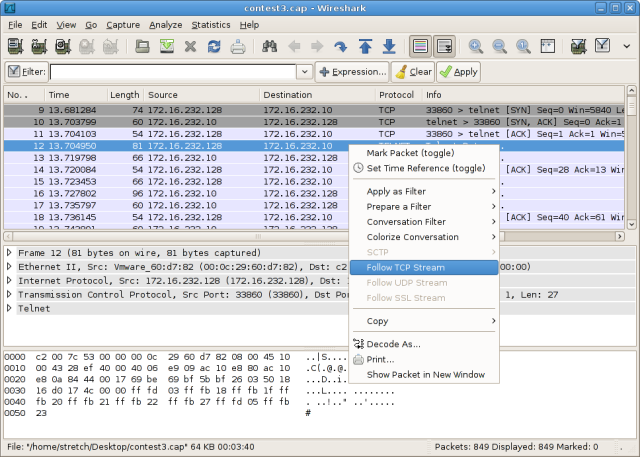
The compiled data will show both directions of the TCP stream. Because the VTY echos back most keystrokes, this can look a bit messy. By filtering out only traffic from the host to the router (select the appropriate direction from the selection list toward the bottom of the window), we can more easily see exactly what was typed in the Telnet session.
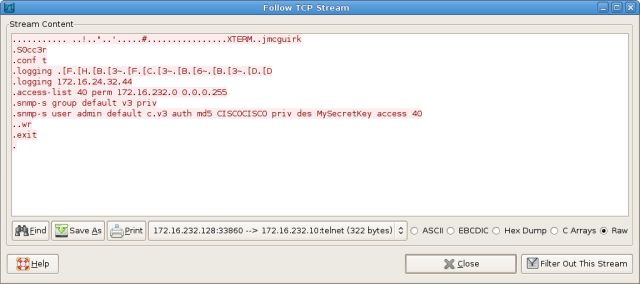
It seems user jmcguirk configured a syslog server, created a standard access list, and enabled remote management of the router using SNMPv3. None of this directly helps us determine the IOS version running, so we'll have to look elsewhere in the capture.
Unfortunately, the only other packets of note contain OSPFv2, OSPFv3, PIMv2, IGMPv2, and some encrypted SNMPv3. The routing protocols and IGMP won't be of any help, but the SNMPv3 credentials we gleaned from the Telnet session can actually be used to decrypt the SNMPv3 requests and responses. Let's take another look at the command used to create user "admin" for SNMPv3 access:
snmp-server user admin default v3 auth md5 CISCOCISCO priv des MySecretKey access 40
The highlighted portions of the command specify the authentication credentials and privacy (encryption) key used. Specifically, an SNMPv3 agent can authenticate with the username "admin" and the password "CISCOCISCO", with MD5 selected as the hashing algorithm (versus SHA-1). Privacy is provided by DES encryption using the string "MySecretKey".
These values can be plugged into Wireshark to facilitate automatic decryption of eligible SNMPv3 traffic. Navigate to Edit > Preferences and select SNMP from the Protocols list at left.
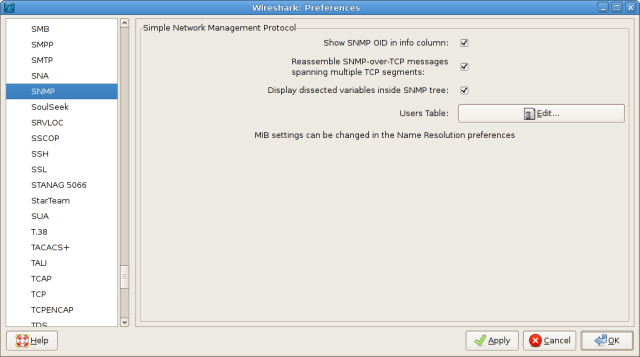
Click the Edit button to modify the SNMP users table. If you haven't modified this table in the past, it should be empty. Create a new user and fill in the values from the IOS configuration command above (engine_id can be left blank).
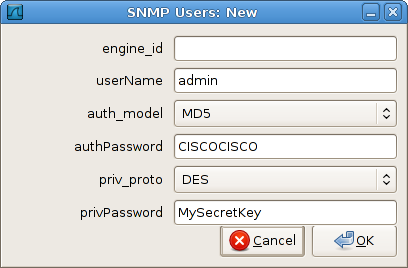
Confirm out of the dialogs until you fall back to the main window, and be sure to remove the display filter (from the Telnet traffic) if you haven't already. The SNMP traffic starts at packet #804. With the SNMP credentials recorded in Wireshark, the SNMP packets are now automatically decrypted, allowing us to read the OIDs referenced and the values returned for each.
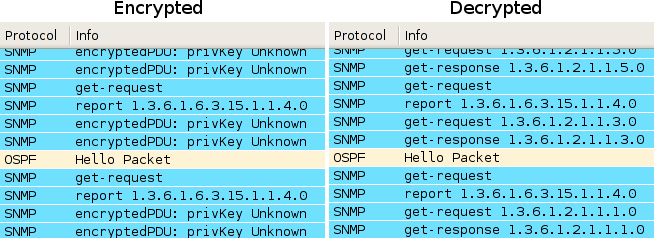
After decrypting the packets, we can see three OIDs were requested from the switch. Using Cisco's MIB browser, we can identify the purpose of each:
- 1.3.6.1.2.1.1.5.0 - System name
- 1.3.6.1.2.1.1.3.0 - System uptime
- 1.3.6.1.2.1.1.1.0 - System description
System description, eh? The response to this GET request can be found in the decrypted payload of packet #816, along with the contest answer:
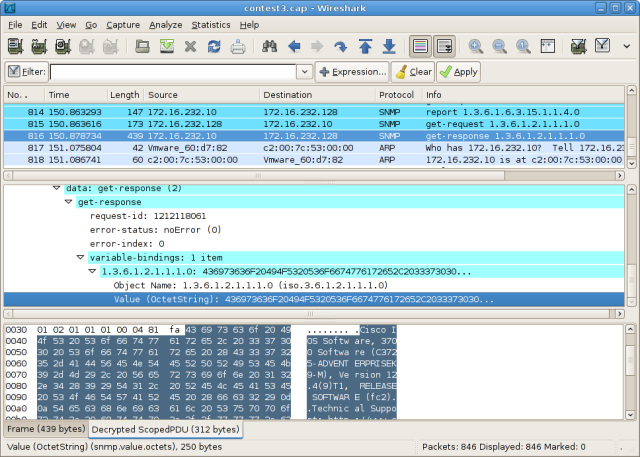
Here's the payload exported as printed text for easier reading:
0000 43 69 73 63 6f 20 49 4f 53 20 53 6f 66 74 77 61 Cisco IOS Softwa 0010 72 65 2c 20 33 37 30 30 20 53 6f 66 74 77 61 72 re, 3700 Softwar 0020 65 20 28 43 33 37 32 35 2d 41 44 56 45 4e 54 45 e (C3725-ADVENTE 0030 52 50 52 49 53 45 4b 39 2d 4d 29 2c 20 56 65 72 RPRISEK9-M), Ver 0040 73 69 6f 6e 20 31 32 2e 34 28 39 29 54 31 2c 20 sion 12.4(9)T1, 0050 52 45 4c 45 41 53 45 20 53 4f 46 54 57 41 52 45 RELEASE SOFTWARE 0060 20 28 66 63 32 29 0d 0a 54 65 63 68 6e 69 63 61 (fc2)..Technica 0070 6c 20 53 75 70 70 6f 72 74 3a 20 68 74 74 70 3a l Support: http: 0080 2f 2f 77 77 77 2e 63 69 73 63 6f 2e 63 6f 6d 2f //www.cisco.com/ 0090 74 65 63 68 73 75 70 70 6f 72 74 0d 0a 43 6f 70 techsupport..Cop 00a0 79 72 69 67 68 74 20 28 63 29 20 31 39 38 36 2d yright (c) 1986- 00b0 32 30 30 36 20 62 79 20 43 69 73 63 6f 20 53 79 2006 by Cisco Sy 00c0 73 74 65 6d 73 2c 20 49 6e 63 2e 0d 0a 43 6f 6d stems, Inc...Com 00d0 70 69 6c 65 64 20 57 65 64 20 33 30 2d 41 75 67 piled Wed 30-Aug 00e0 2d 30 36 20 31 38 3a 34 38 20 62 79 20 70 72 6f -06 18:48 by pro 00f0 64 5f 72 65 6c 5f 74 65 61 6d d_rel_team
Winners
Congratulations to the randomly-selected winners of Routing TCP/IP volume 2!
- Bry Ashman
- Daniel Percy
- Peter Myers
I'll be in contact shortly to arrange shipment of your books. Many thanks to Cisco Press for sponsoring these prizes!
So, thoughts on the contest? Too easy? Too hard? Let me know!
Posted in Announcements
Comments
January 9, 2009 at 11:04 a.m. UTC
if we take time needed to solve the contest as difficulty factor then it's too easy
January 9, 2009 at 11:18 a.m. UTC
Excellent, its good to see the answer. I had found all the encryption keys on the telnet packets and was looking on the internet for some way for decrypting the packets, little did I know it could be done within Wireshark! Hey ho.
Looking forward to the next one!
January 9, 2009 at 11:54 a.m. UTC
I thought it had something to do with the "Data not conforming to RFC3411" in the router's EngineID. Cisco has encoded some extra data in there. I didn't think to look in the telnet traffic!
January 9, 2009 at 12:38 p.m. UTC
Armed with credentials the most time I spent on it was searching the web for tool to decode it. Fortunately I arrived at protocol settings in Wireshark after couple of painful hours :). Definitely the most exciting contest, congrats for the winners!
January 9, 2009 at 12:51 p.m. UTC
Hi Jeremy,
it was a great contest for me too - and found it also. Can u post some statistics about how many readers are have the the right solution of the january contest?
Thanks!
January 9, 2009 at 1:50 p.m. UTC
As for the stats, we had 93 correct entries, and about a dozen incorrect or late entries. Most of the incorrect entries seemed to use profiling against the traffic capture to guess which IOS version was running.
January 9, 2009 at 1:55 p.m. UTC
I think this one was pretty easy ( at least for people that already had messed with a capture file from a telnet session to get fellow coworkers Acs password just for messing with them ;) ), the part about the decode of the snmp packets in Ws was the most hardest part as i had never done that.
January 9, 2009 at 3:52 p.m. UTC
That was pretty interesting, definitely an opportunity to learn something new!!
January 9, 2009 at 4:00 p.m. UTC
Nice contest ! Learn a lot. Even went back to do the previous one. We want some more !
January 9, 2009 at 4:59 p.m. UTC
Yeah I was unsure how to get to the answer. Was a good learning experience for me! Looking forward to the next one!
January 9, 2009 at 5:23 p.m. UTC
Great contest!
January 9, 2009 at 5:41 p.m. UTC
never thought wireshark can be used to decrypt packets. really amazing...thanks.
January 9, 2009 at 5:45 p.m. UTC
Great challenge. I learn a lot from this site. Being at not quite the level to have a clue on my own on how to participate in this type challenge, would it be possible to host a simpler style challenge as well without prizes but simply to get people like me hacking and slashing instead of simply waiting for contest answers?
Thanks for a great site!
January 9, 2009 at 5:50 p.m. UTC
I absolutely love these contests, even if i get them totally wrong. :)
January 9, 2009 at 5:50 p.m. UTC
I thought this one was a little easy if you had previous experience with Wireshark. I didn't know it could decrypt SNMP packets though, so it was worthwhile for me. Also it wasn't so ridiculously hard (like that time one) that I wasn't even sure where to start. Overall I enjoyed it. Keep 'em coming.
January 9, 2009 at 6:31 p.m. UTC
This contest wasn't easy, but it wasn't hard either. The key was knowing your how to use your toolset. I spent way too much time searching for a way to decrypt SNMPv3 packets when Wireshark will do it for me.
January 9, 2009 at 8:11 p.m. UTC
Very well thought out puzzle - didn't have the time to dig around in the capture this time, but these contests are always neat to see.
January 9, 2009 at 8:26 p.m. UTC
Yes, I can agree that was the easiest one, but was very interesting too. I didn't know that wireshark is able to do that but it was on the first page when I google it.
http://www.google.bg/search?q=decrypt+SNMPv3+packets
Keep in that way Stretch ! I'm sure that each one of us has found something to learn during your contests. Thank you man ...
Best wishes,
Danail Petrov
January 10, 2009 at 4:32 a.m. UTC
I also spent a lot of time looking for some other freeware application that would decode the SNMP packets since I was sure the answer was there. Some Google searching turned up a User Table option in Wireshark I had not known was there. I began poking around Wireshark and discovered a place to put in the information I had copied down from the telnet packets.
I realized later I sent in my entry with the subject line "January contest" instead of just "contest" so hopefully my entry was counted but if not I learned something new which made this all well worth it.
Great contest and I look forward to the next one!
Dave
January 11, 2009 at 9:34 a.m. UTC
Very good contest! I enjoyed it very much, keep up the contests they are a unique and fun way for users to interact with your site.
January 12, 2009 at 10:33 a.m. UTC
Hey Jeremy :)
Nice Job as usual :D
Here is one topic idea that you could (should !!! :D ) use : Teach us how to use wireshark on Switched network :)
I mean : i want to sniff fa0/1 on router A and i'm fa0/48 on router D :D
Thanks :)
January 12, 2009 at 3:39 p.m. UTC
I would agree with most of the others, it took maybe 10 mins to 'find' the answer but >30 Minutes to actually decode it from the SNMP. I'm guessing most people didn't know or at least never used the SNMP decoding features on wireshark. I would also say the large number of correct responses would indicate that either the challenge was easier or it was just more people answered. What was the ratio of correct answers to downloads compared with other challenges? Definitely looking forward to the next one, I always end up learning something.
January 13, 2009 at 2:08 p.m. UTC
Very interesting, Ive just stumbled accross this site and I look forward to some more of these :D
